What is Pentesting?
Pentesting, also known as penetration testing, is a security testing approach where a team of cybersecurity experts simulate real-world cyberattacks to identify security vulnerabilities in computer systems, networks, and applications.
By performing pentesting, organizations can proactively identify potential security risks and take appropriate measures to mitigate them before attackers exploit them.
Our team of pentesting professionals uses the latest tools and techniques to identify vulnerabilities in your organization's systems and provide you with a comprehensive report detailing the identified vulnerabilities and recommended remediation actions.
Why do you need Pentesting?
- Pentesting is a crucial component of a comprehensive cybersecurity strategy. Here are some reasons why your organization needs it:
- Identify security vulnerabilities: Pentesting can help you identify security vulnerabilities in your computer systems, networks, and applications that could be exploited by attackers.
- Mitigate potential risks: By identifying and remediating vulnerabilities before attackers can exploit them, you can reduce the risk of a successful cyberattack and its associated costs.
- Comply with regulations: Many industries and regulatory bodies require regular pentesting to ensure compliance with security standards and regulations.
Expert Pentesting Services
We use the latest tools and techniques to identify vulnerabilities in your systems and applications.
Cost-Effective Solution
Hiring a full-time pentesting professional can be expensive, especially for small to medium-sized businesses.
Flexible and Customizable
Our pentesting services are flexible and customizable to meet the specific needs of your organization.
What does Pentesting involve?
Vulnerability Assessment
Our platform identifies vulnerabilities in your systems, networks, and applications using automated techniques.
Web Application Penetration Testing
Our team performs manual and automated testing of web applications to identify vulnerabilities and provide recommendations for remediation.
Network Penetration Testing
Our team platform performs automated testing of your network to identify vulnerabilities and provide recommendations for remediation.
Mobile Application Penetration Testing
Our team performs manual and automated testing of mobile applications to identify vulnerabilities and provide recommendations for remediation.
Report Generation and Recommendations
We provide a comprehensive report detailing the identified vulnerabilities and recommended remediation actions.
DMZ Penetration Testing
Our team platform performs automated testing of your DMZ to identify vulnerabilities and provide recommendations for remediation.
What are compliance prep tools?
Compliance preparation tools are designed to help organizations prepare for regulatory compliance. These tools can help identify gaps in your organization's compliance posture, and provide recommendations for addressing those gaps.
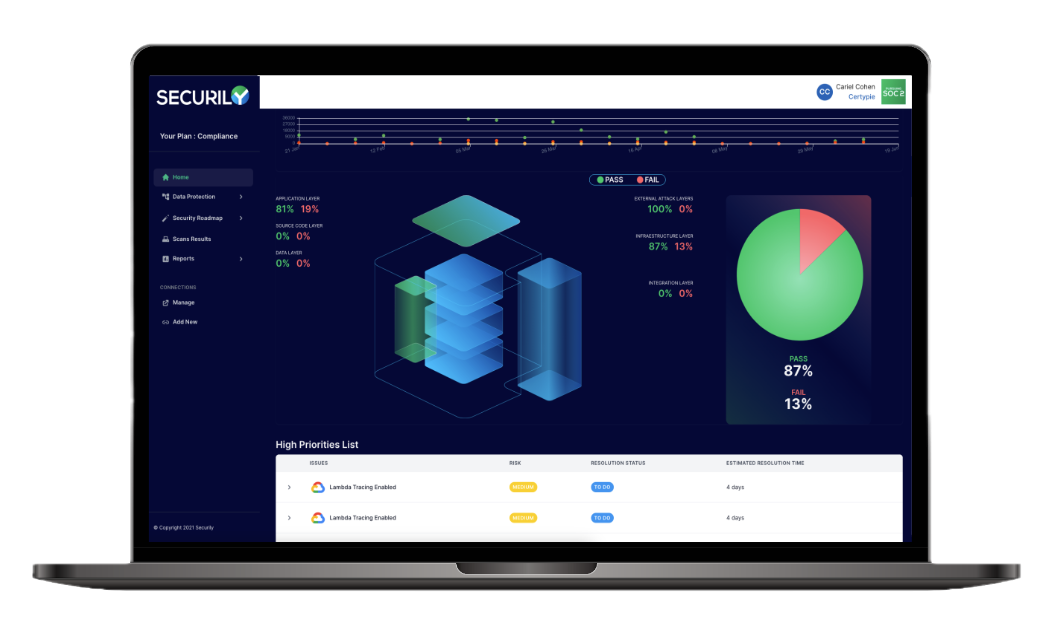
How does it work?
We don't want you to miss the biggest customer of your life
Tech Founders develop innovative products that solve costly problems and attract life changing buyers. But their security compliance can slow the buying process to a point that they lose their biggest opportunities.

The team at Securily helped us go through our open findings and understand our security posture, our Customer Success manager helped us craft a strategy that was doable for our tech team. We were able to not only win the confidence of the customer, but get the deal as well.
#growth #cybersecurity #strategy

Joseph Estrada
CTO & Co-Founder at DiscoWe enjoyed working with Securily's engineering team to craft our data processing schema engine for our APIs as well as securing authentication on AWS Lambda, their engineers provided with security insight that would have otherwise consumed countless hours of research.










